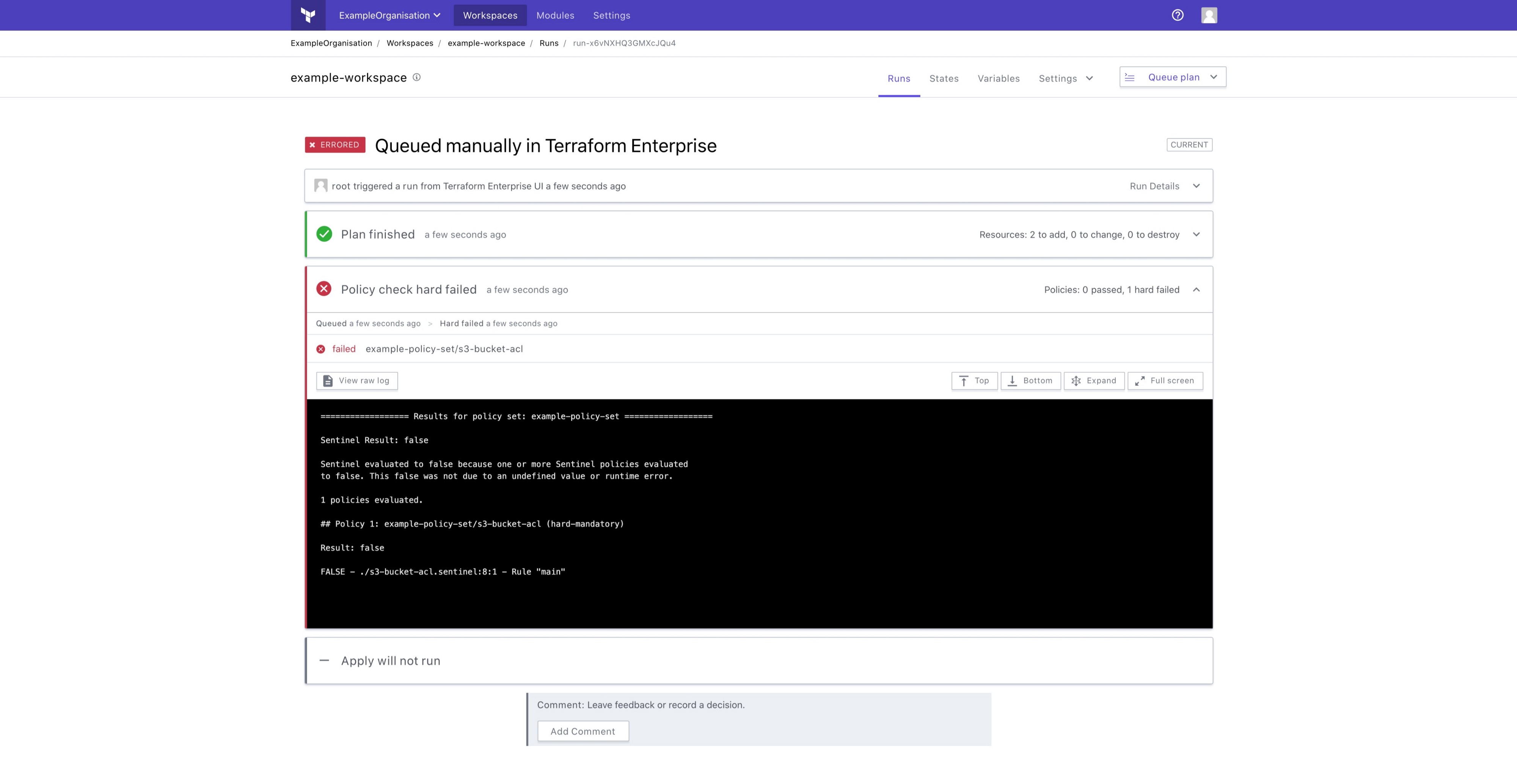
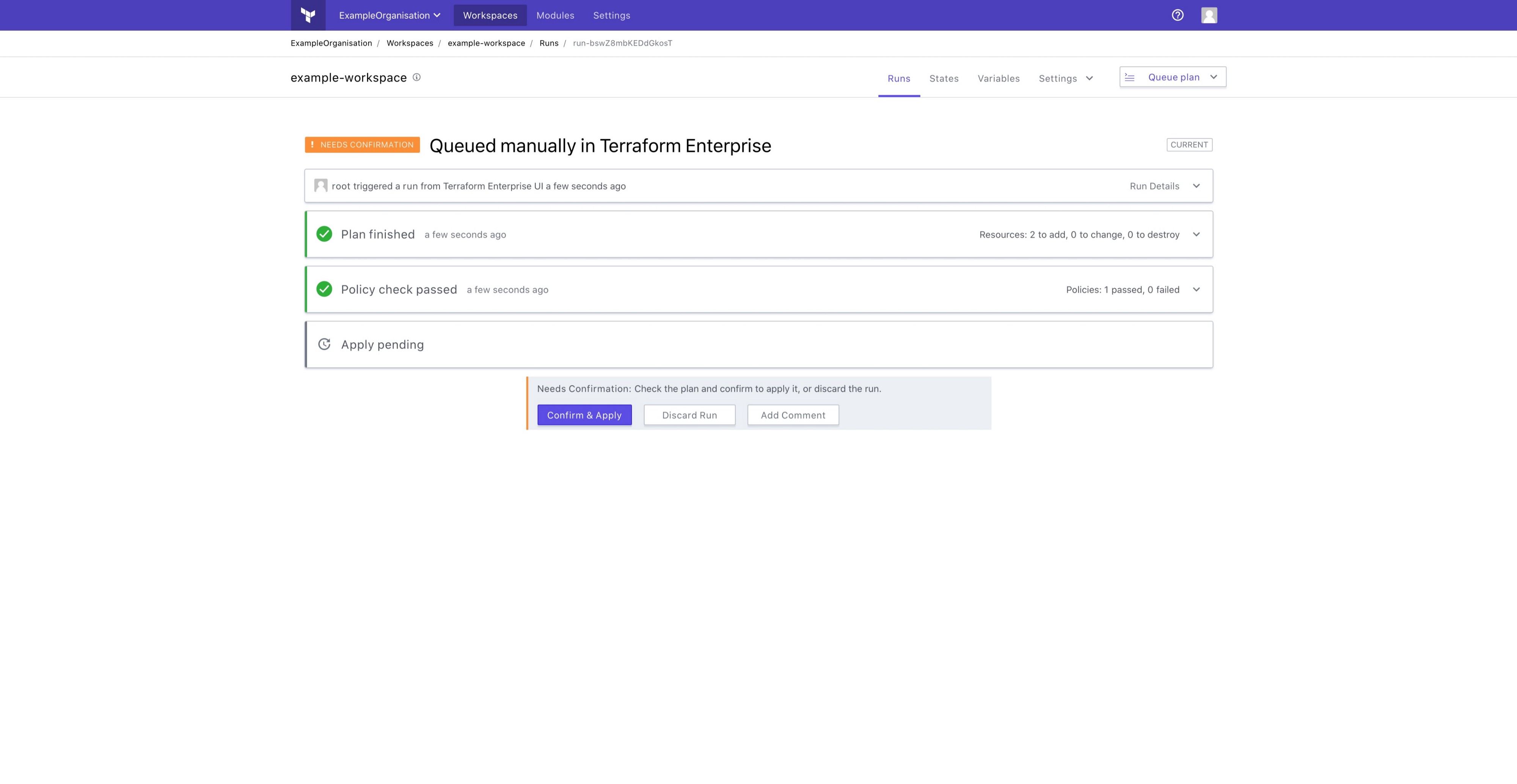
The Anatomy Of A Sentinel Policy
Before we look at a real world example, let’s first take a quick run-through the basics of a Sentinel Policy definition.
Sentinel Policies are written in a subset of the Hashicorp Configuration Language, or HCL for short. At the most abstract level, a Sentinel Policy looks like the following:
import "..."main = rule {
...
}
import — The import statement allows a policy to access reusable libraries and data sources available within the policy execution environment. The following imports are available within Terraform Cloud:
- The standard Sentinel Imports — These allow access to common functions such as string manipulation, math functions, HTTP client creation, etc.
tfconfig — Allows you to access information about the Terraform code being executed.tfrun — Allows you to access information about the run-time environment for the current Terraform execution.tfplan — Allows you to access information about the planned changes within a Terraform execution.tfstate — Allows you to access information about the stored state associated with an applied Terraform run.
main — Every policy must have a rule named main. This rule acts as the entry point for the policy execution.
rule — Rule blocks contain the conditions and evaluation logic which form the tests within a policy. Rules must return a boolean value depending on whether the rule is successful (true), or is disallowed (false).
Individual policies are stored within distinct files, usually with a .sentinel extension.
A very basic, working policy might look like the following:
import "tfconfig"
main = rule {
tfconfig.modules.mymodule.version is "~> 1.0"
}
Here you can see that we are importing the tfconfig library, giving us the ability to inspect the Terraform code we are applying. Within our main rule we are specifying a check that our mymodule instance is referencing an allowed version. Again, if any code is encountered which contradicts this rule, then the policy is marked as failed.
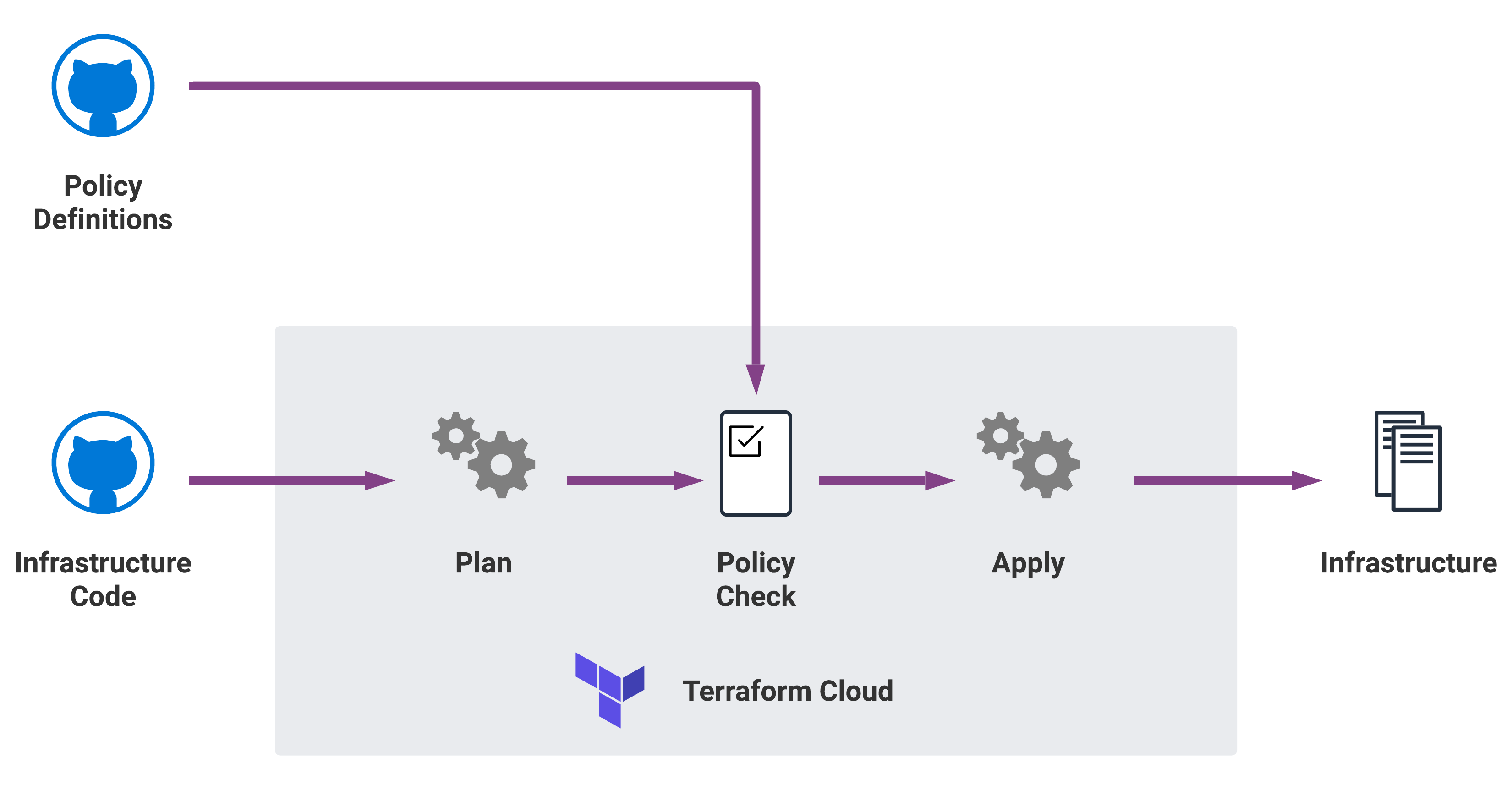
Once you have defined your policies, you must also create a Policy Set. A Policy Set is a HCL file defining the policies to be evaluated in order. Each policy is referenced within a policy block containing a relative link to the policy file, along with the enforcement level for the policy. For example:
policy "my-policy-1" {
source = "./policies/policy-1.sentinel"
enforcement_level = "advisory"
}
policy "my-policy-2" {
source = "./policies/policy-2.sentinel"
enforcement_level = "hard-mandatory"
}
policy "my-policy-3" {
source = "./policies/policy-3.sentinel"
enforcement_level = "soft-mandatory"
}
A Policy Set file must be named sentinel.hcl. When stored together, the directory structure associated with the example Policy Set above might look like the following:
/
├─ policies/
│ ├─ policy-1.sentinel
│ ├─ policy-2.sentinel
│ ├─ policy-3.sentinel
├─ sentinel.hcl
To help accelerate consumers in building their policy libraries, Hashicorp provide examples of the recommended directory structure, alongside useful reusable policy functions and sample policies in their terraform-guidelines repository, here.