I was recently asked to conduct phishing tests against our own Airwalk employees to assess our susceptibility to attack. We didn’t want to spend money engaging a third party testing company because, as a technology company, we thought we could probably do it ourselves. In another story, I describe the technical steps I took to achieve this using open source tools, in case you want to do something similar yourself. Here I will keep it as non-technical as possible. Before I launched myself into the murky world of fake emails and dodgy links, I felt that it was important to consider our approach and what we were aiming to achieve.
Training
You need to give people the chance to succeed, so before I sent any email I wanted to be sure that we had given everyone some anti-phishing training and taught them what to do if they are ever suspicious of something they receive.There are many online training courses available, from a range of paid ones right down to this really handy and short quiz from Jigsaw / Google.
 Aside: Send that to your entire family right now.
Aside: Send that to your entire family right now.
As well as just sending out the training, we waited for everyone to confirm that they had completed it. I created a new email address for anyone to forward any suspected phishing emails that they may receive. We told everyone about this too.Finally, in the interest of complete openness, we decided to warn the whole company that we will be performing phishing drills in the coming weeks.
How do I construct a phishing email?
Regardless of the tools used to send it, I had to consider what form we wanted our “test” or “drill” emails to take.
Common phishing
There are so many options here. You could send an email pertaining to be from a large service provider, such as Google, Hotmail or PayPal, telling users that their account is locked, or there was some suspicious activity they need to look at, all of which end with a user being encouraged to click a link or open an attachment. Other approaches could be something where the recipient is so overwhelmed by a feeling of there being something good or interesting about to happen that they let their guard down and just click the link or attachment. Examples here are new contact requests or messages from social media sites, a missed parcel from a courier company, a large deposit into a bank account, etc. Frankly, these approaches feel a bit passé and I would hope our people wouldn’t fall for them.
Spear Phishing
My favoured approach for our first “attack” was to send something that was claiming to be from within Airwalk, a technique known as spear phishing, presumably due to it being very specifically targeted. This vector raises a lot more questions to ask oneself.Assuming your corporate email systems and DNS are configured correctly, any email claiming to be from inside the company (Maybe pertaining to be from the HR department, or a senior member of staff) can’t be sent from a genuine company email account or company domain. If someone is suspicious and checks the origins of the email or the ownership of the domain and finds it to be genuine, we can’t then tell them they’ve failed a phishing drill.
The emails also can’t contain any information that couldn’t be found publicly. Where you draw the line here is hard and comes down to who you think your enemy is. Any ex-employee will have much more information at their fingertips than a supplier or customer, who in turn would have more than an individual who has had no legitimate contact with you. I decided we would focus on the unknown internet bad guys. They could probably get staff names and job titles from LinkedIn, they would be able to get your corporate branding, your address and a feel for your type of business from your website and some names and addresses from company lookup sites or Google. They would also be able to know which email provider and perhaps other online services you use from DNS.
If you’re a large company which sends emails to thousands of customers or posts regularly to public mailing lists, then it wouldn’t be unreasonable to use a genuine email signature or footer on your phishing email as this is already in the public domain. If your company only really emails a small number of clients or suppliers, it’s probably not reasonable to expect a phishing email from an unknown attacker to use an accurate company signature. Of course, if an ex-employee or someone associated with a client or supplier is involved, things could get much more targeted, so use your judgement here.
Whaling
For completeness, I’ll mention whaling here. Whaling is a more specific form of spear phishing where the target of the email is a senior executive and the content of the email is usually much more specific, for example the threat of a lawsuit or an official governmental notice of some kind, often with a sense of urgency. The reason executives are targeted is that the potential prize is much bigger — they will have access to juicy, confidential company data so compromising their computer, or getting them to accidentally hand over their passwords, would give the bad guys a great day at the office. Also, it’s often easier to find personal information about senior executives as their names are well known, their profiles will be on the corporate website, in some countries they have to publish their tax affairs, etc. That simplifies the process of writing a convincing sounding email to these individuals. I wasn’t planning on doing any whaling myself.
Domains
As discussed above, I didn’t want to use our genuine company email systems, so I decided to purchase a new internet domain, as any external attacker could, which was similar to our corporate domain. I chose airwalk-consulting.com which is identical to our domain but with a hyphen between the two words. I purchased it from a different registrar and used different registrant details to our company domains. Ten minutes and £8 later I was in business. As an act of defence against copycat or activist websites, a lot of larger companies buy up similar sounding domain names just to keep them off the market. While it probably isn’t their primary reason for doing so, it will also help them against phishing.
What are we testing?
If I were to just fire an email into the company from a domain name that nobody at Airwalk had ever had contact with, it would almost certainly end up being caught by the mail server’s spam filter and land in a junk folder with a red warning across the top. While this proves our automated defences are working fine, it doesn’t help us test the weaker part of the system — the humans. Should I deliberately remove this technological layer of protection for my phishing test domain? Of course! We know there is reasonable technology out there to block suspicious email and hopefully we’re all using some of it, but what we’re here to test are the people. Therefore, I should whitelist my copycat domain on our corporate mail server. Doing so may increase the number of people who will know that an attack is coming and what form it will take. After all, the people in your IT department who would have to make the changes to the corporate mail server probably aren’t the same people who are arranging the phishing test, but that depends on your company structure.
The clues are there
Back to enabling our colleagues to succeed, and bearing in mind I was about to launch the first of potentially many phishing tests, I shouldn’t create an initial email that is so super-convincing that you’d have to be Poirot to spot it. I wanted to leave enough clues that anyone who was awake and had consumed their morning coffee could correctly call “phish”. My first email invited our company to read all about Airwalk’s Brexit planning via a link pertaining to be to our intranet. This was not an original idea, as phishers are known for choosing popular topics from current affairs to pique people’s interest and to distract them from considering the validity of the sender. The clues I left them were:
- While the email “from” friendly display name was the name of one of our Directors (easily found on our website), the email address it was sent from was not his address, it was the generic info@ address mentioned on our “Contact Us” page
- The domain part of the email address was the fake one I purchased, not our company email domain
- The term I used to refer to the link was “the intranet”. We do not use this term within the organisation
- For anyone looking very deeply, the email originated in Brazil. We have no business in Latin America
The end of the rainbow
Another question to ask is what happens when someone actually clicks the link. They will go to a page I have crafted, but what should it contain? For some test attacks, we could encourage people to input data, maybe a fake login page for a service, but then we would be accepting passwords, which doesn’t feel great to me. At some point you should probably reveal that the user has been participating in a phishing test, otherwise they’re going to end up frustrated or confused.
I created a simple target page, seen by those who took the bait, which clearly stated that the reader had participated in an Airwalk phishing test, but I still couldn’t resist having Matrix-style green rain falling in the background.
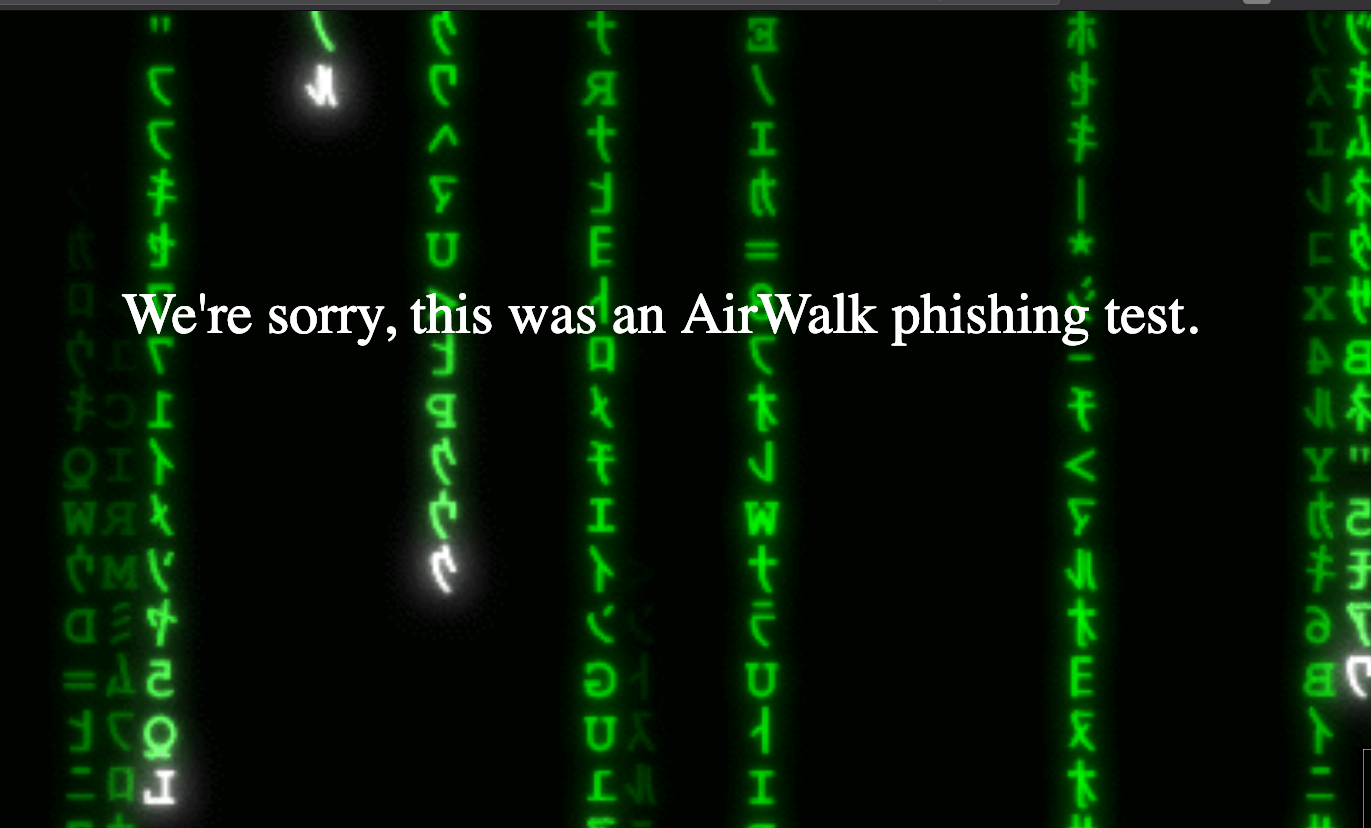 My phishing test landing page
My phishing test landing page
Timing is everything
I also considered when to send the email. If I send it during the middle of the day when the office was full, there is a strong chance that people would start talking out loud about it and then the whole office would become aware of what was happening, giving me a false reading of the company’s response as a whole. I therefore sent it early in the morning, so people would discover it as they got to the office, or perhaps on their mobile phones on the train.
Something smells phishy
In order to limit the potential for office chatter alerting people who had not yet checked their emails, I monitored the results carefully using my chosen phishing tool (details in a later story) and pulled people into a private Slack channel as they each opened the email. In that channel I requested that people keep any conversation about the email to that specific place and not on more general channels or openly in the office.
Feedback
To make the tests effective, feedback to our colleagues is essential. They shouldn’t be left feeling that they’ve been caught out, or failed a test that will somehow negatively impact them in the future. At a company all-hands event which occurred the following week, I talked about how well we did collectively, what we should all be looking out for and introduced another training course that we will be asking everyone to complete before I launch another test. No names were named.

Anyone for fish?
 Aside: Send that to your entire family right now.
Aside: Send that to your entire family right now. My phishing test landing page
My phishing test landing page