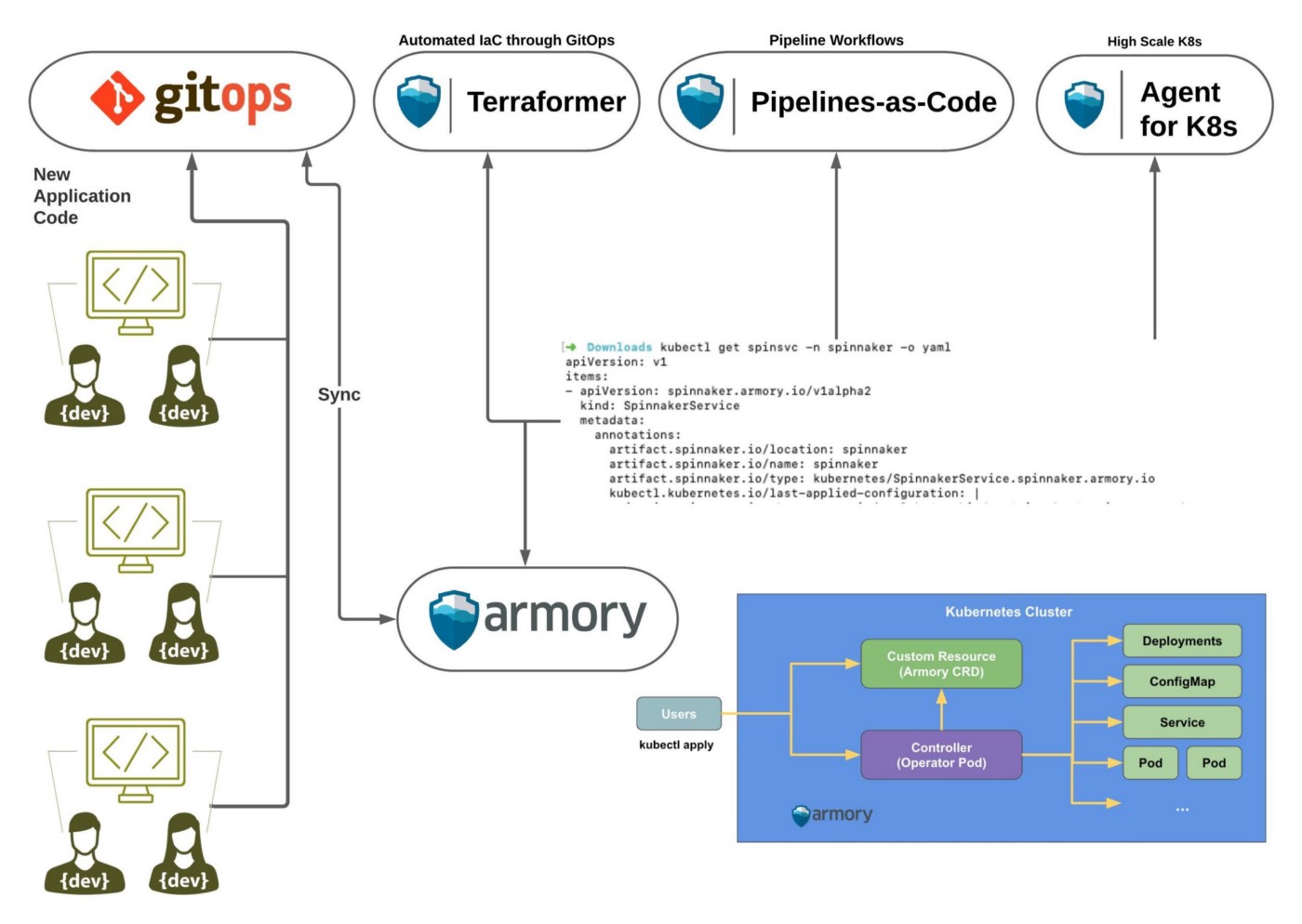
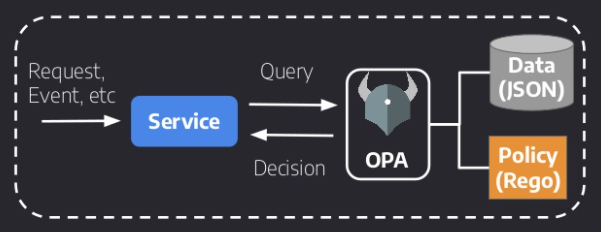
-
Services
-
Sectors
-
Financial Services
Transforming the financial services sector with industry-leading cloud and data solutions.
Read More
-
Public Sector
Delivering compliant and secure cloud automation solutions for the Public sector.
Read More
-
Other Sectors
Other sectors that we currently have clients within include insurance, media, retail, construction and automotive.
Read More
-
Case Studies
-
Partners
Insights and News
-
About Us
-
Leadership Team
Our team of industry-leading experts deliver world-leading transformation solutions.
Read More
-
Office Locations
We would love to talk about transforming your business. Please let us know.
Read More
-
Insights and News
Our latest industry news, insights, employee stories, and upcoming events.
Read More
-
Careers
Contact Us