Security Information and Event Management (SIEM) systems, such as Splunk, QRadar and LogRhythm, to name just a few market leaders, are powerful tools for security teams to detect threats, investigate incidents and respond quickly to malicious activity. A SIEM tool can help identify security threats, support incident response efforts, and meet compliance requirements. They can be used to collect data from multiple sources such as networks, servers, applications, and endpoints to create a comprehensive view of an organisation’s user activity within their on-premises or cloud environment. However, many organisations are still treating their SIEM tool as just an expensive data pump, instead of taking full advantage of supplementary cloud native capabilities.
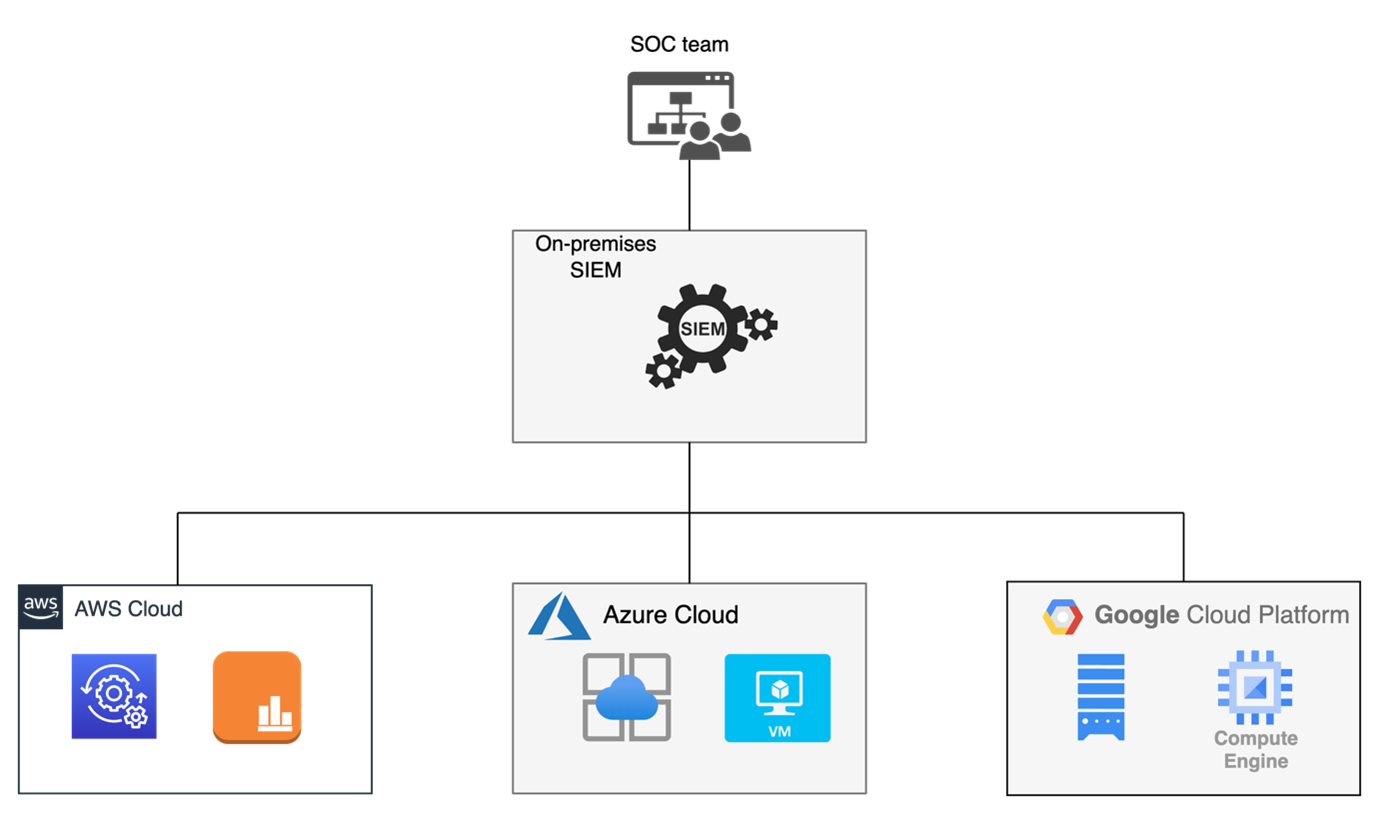
Diagram 1. SIEM data flow from cloud environments.
Go Native
Cloud security is an important consideration for businesses of all sizes. With the increasing reliance on cloud computing, organisations need to ensure that their data and applications are secure from malicious actors. Two popular cloud security solutions, and cost-effective must haves, to supplement expensive third-party SIEM tools are Microsoft Azure Defender for Cloud and Amazon Web Services (AWS) GuardDuty.
Microsoft’s Arc enabled multi-cloud native Defender for Cloud, is now categorised as a Cloud Native Application Protection Platform (CNAPP), this includes a wide range of security services such as Cloud Workload Protection (CWP), DevOps Security, Cloud Security Posture Management (CSPM), Cloud Infrastructure Entitlement Management (CIEM), Entra Permissions Management, Secure Score, Policy Management, Resource Inventory, Security Graph, Cloud Explorer, External Attack Surface Management, Azure Network Security and Microsoft Defender Plans, including; Servers (Qualys Vulnerability Management), Storage, SQL, Containers, App Service, Key Vault, Resource Manager, DNS and 365 Defender. The Arc enabled Defender for Cloud and Sentinel SIEM solution provides a multi-cloud single portal that integrates all these CNAPP services, enabling SOC teams to monitor and assess all their cloud and on-premises environments within a single holistic view to detect malicious activity and provide an automated incident response.
Spend OpEx not CapEx
The combination of Microsoft’s Defender for Cloud and Sentinel SIEM solution integrates comprehensive security orchestration, automated incident response, data protection in multi-cloud storage and SQL database resources, across PaaS, IaaS, as well as third party such as Mongo DB and other open-source databases. This integration will detect potential threats to cloud infrastructure and data, such as brute-force attacks, SQL injection, and suspicious data extraction. The added financial advantage of cloud native tools, is that they can be tried and tested as an Op Ex cost, turned off with ease if not fit for purpose, or further streamed into an on-premises SIEM tool for supplementary or enterprise level analysis. It is always worth trying these native tools first before committing eye watering CapEx to an on-premises SIEM tool that will require ongoing investment, Security Operations Centre (SOC) analyst resources, training, and system maintenance. Microsoft’s new Security Co-Pilot is also an interesting development being marketed as an AI enabled SOC assistant. It uses OpenAI’s large language model (LLM) combined with a security specific AI model built by Microsoft. This will be something to keep an eye on in the future.
Both services, Azure Defender for Cloud and AWS GuardDuty are Platforms as a Service (PaaS). They both offer comprehensive protection against threats such as malware, unauthorised access attempts, and data breaches. However, there are some differences between them that should be considered when choosing a solution for your organisation's needs. Azure Defender for Cloud offers advanced threat detection capabilities, in addition to its built-in cloud Security Posture Management (CSPM) and the Defender analytics engine, which can detect anomalous behaviour in user accounts or system activity across on-premises networks, or multiple clouds including Azure itself, as well as other hybrid private on-premises clouds and public clouds such as AWS or Google Cloud Platform (GCP). It provides continuous monitoring of network traffic to identify and send alert for suspicious activities such as brute force attacks or resource compromises in real time so analysts can take immediate action if necessary. It also integrates with many third-party SIEM tools, which allow SOC teams to collect event logs from various other on-premises sources into one centralised platform, where they can be analysed more efficiently than if done manually by SOC analysts alone.
For more information, read the following Microsoft blog The next wave of multicloud security with Microsoft Defender for Cloud, a Cloud-Native Application Protection Platform (CNAPP).
Multi-Cloud Sec Ops
Additionally, AWS GuardDuty is very easy to implement and uses machine learning algorithms combined with threat intelligence feeds to detect malicious activity quickly and accurately within an AWS environment, without requiring any manual intervention from SOC analysts. It has integration capabilities with other SIEM tools but does not have its own native analytics engine like Azure Defender for Cloud, making it less powerful at detecting control gaps and configuration anomalies compared to its competitor. Furthermore, GuardDuty only works within the confines of AWS’s ecosystem meaning customers must use additional third-party solutions if they wish to protect resources outside this platform.
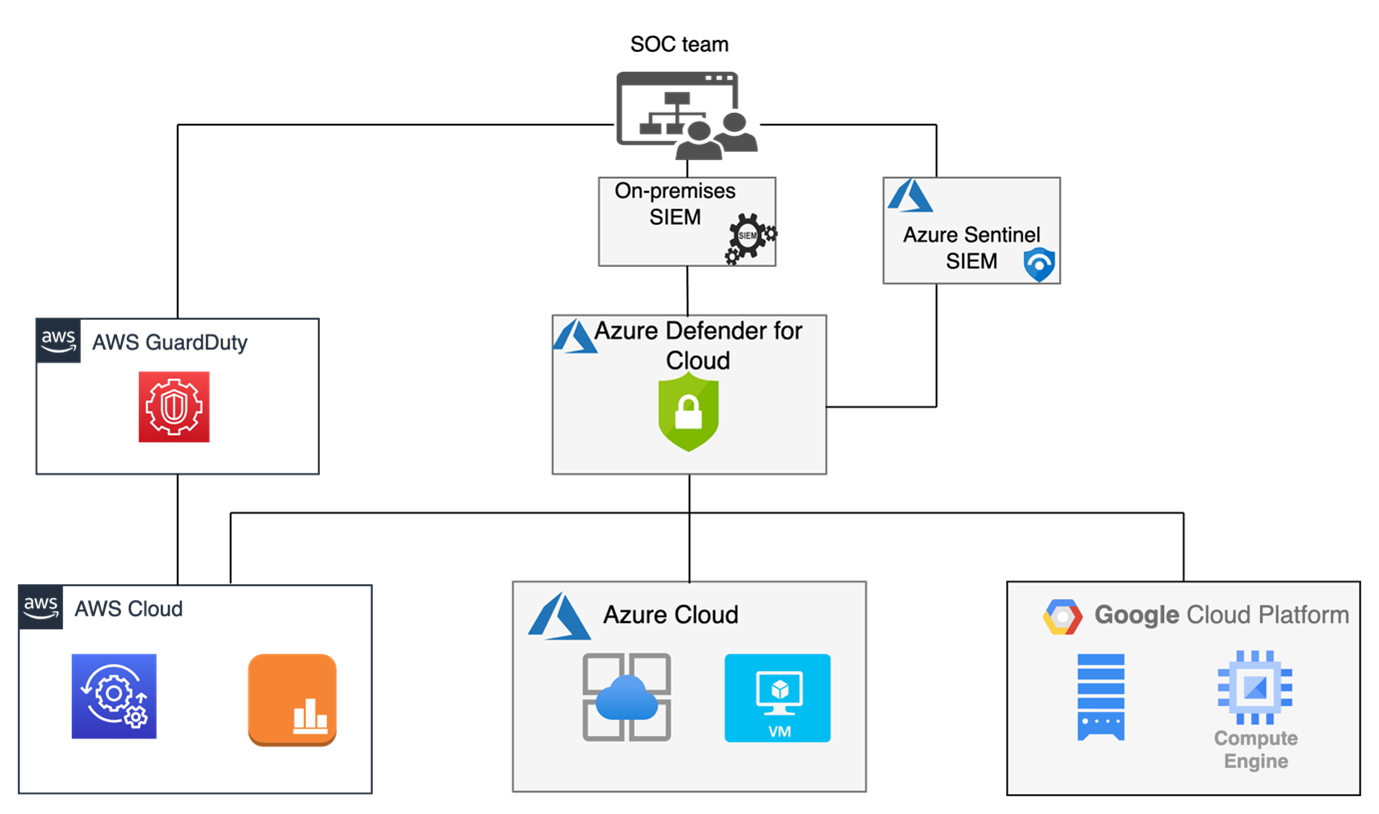
Diagram 2. Cloud native detection and alerting integration with SIEM data flow.
In conclusion, both Azure Defender for Cloud and AWS GuardDuty when deployed together provide a comprehensive defence in depth against potential threats, however each has different strengths depending on what type of environment an organisation operates in. Therefore, when selecting a solution, organisations should consider factors such as cost, effectiveness, multi-environment monitoring, scalability and support options before deciding on either service.
Of course, it is up to the organisation to determine how best to utilise their SIEM tool to meet their specific security needs. However, it is not uncommon for organisations to unintentionally use their SIEM tool as a data collection and storage platform, without optimising its functionality and actively using it to analyse and respond to security events. This can happen for a variety of reasons, such as a lack of enterprise resources to effectively use the SIEM tool, or a focus on compliance rather than proactive security.
The primary purpose of a SIEM should not only be collecting data, but also analysing it for potential security risks or incidents that could threaten the integrity or confidentiality of data and its associated systems. All too often companies and organisations focus on merely getting logs into their SIEM tool without making sure they have sufficient skills and resources available for effective analysis which results in an inefficient use of time and money when trying to identify malicious activity within the network infrastructure. Additionally, if there are not adequately skilled analyst resources with expertise in this area then these alerts may go unnoticed. This could lead to potentially costly ransomware attacks or data breaches occurring, due to incident response plans and processes not being implemented effectively.
Organisations need to understand that simply having access to large amounts of information is not beneficial unless they know how to interpret it correctly and respond effectively in a timely manner. This is where skilled cyber security professional services, such as provided by Airwalk Reply, can help ensure the right tools and procedures are in place to maximize protection, while minimising cost associated with false positives in addition to other issues that arise when dealing with big volumes raw log files, generated by various and multiple sources across the enterprise. To truly benefit from utilising a SIEM technology, security teams must first recognise its value beyond just being a data pump and provide meaningful insights to better secure business operations.
Airwalk Reply Cloud Security Services Read more.

